As it is not desirable to have DCs communicate directly with anything on the internet, the Azure AD Password Protection solution provides a Azure AD Password Protection Proxy Service that acts as an intermediate between the Azure AD Password Protection DC Agents on the DCs and Azure AD. Per AD forest you can implement 2 servers with the Azure AD Password Protection Proxy Service installed.
To install the Azure AD Password Protection Proxy Service, you can use the PowerShell script which will configure use a log file and some nice output. For additional requirements, please see Azure AD Password Protection – Deployment Requirements.
To download the latest version: Azure AD Password Protection for Windows Server Active Directory
To read about the version history and release notes: Azure AD Password Protection agent version history
.\AAD-Password-Protection-Install-Proxy-Service.ps1 –servers <FQDN Server 1>,<FQDN Server 2> -installSourceFullPath "<Full Path To AzureADPasswordProtectionProxySetup.exe>"
–

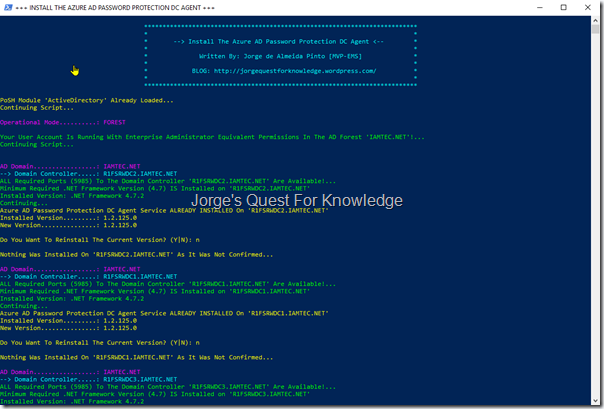
Figure 1: Installing The Azure AD Password protection Proxy Service
–

Figure 2: GridView Output
–

Figure 3: Installation Log File Sample
–
You can download the script from here
–
Just before version 1.2.116.0 Azure AD Password Protection Proxy Service software was an MSI and starting with that version it is an EXE. That’s why the code above supports both.
With version 1.2.116.0 and higher the Azure AD Password Protection Proxy Service software supports automatic upgrade, which is enabled by default.

Figure 2: Checking The Azure AD Password Protection Proxy Service Configuration
–
To disable automatic upgrade, you can use the following command:
Set-AzureADPasswordProtectionProxyConfiguration -AutoUpgradeEnabled $false
… and to enable it again:
Set-AzureADPasswordProtectionProxyConfiguration -AutoUpgradeEnabled $true
–
If auto upgrade is disabled, the Azure AD Password Protection Proxy Service will log an event ID 20002 in the Azure AD Password Protection Proxy Service Operational Event Log mentioning there is a newer version available. With auto upgrade enabled, nothing is logged about a newer version.
–
After installing the Azure AD Password Protection Proxy Service for the first time or after installing version 1.2.116.0 or higher, you need to (re-)register both the Azure AD Password Protection Proxy Service and the on-premises AD forest in Azure AD.
To register the Azure AD Password Protection Proxy Service in Azure AD:
$adAdminAccount = Get-Credential
$aadAdminAccount = Get-Credential
Register-AzureADPasswordProtectionProxy -ForestCredential $adAdminAccount -AzureCredential $aadAdminAccount
If you are already logged on with an Enterprise Admin account for AD, then register the Azure AD Password Protection Proxy Service in Azure AD as follows:
$aadAdminAccount = Get-Credential
Register-AzureADPasswordProtectionProxy -AzureCredential $aadAdminAccount
To register the on-premises AD forest in Azure AD:
$adAdminAccount = Get-Credential
$aadAdminAccount = Get-Credential
Register-AzureADPasswordProtectionForest -ForestCredential $adAdminAccount -AzureCredential $aadAdminAccount
If you are already logged on with an Enterprise Admin account for AD, then register the on-premises AD forest in Azure AD as follows:
$aadAdminAccount = Get-Credential
Register-AzureADPasswordProtectionForest -AzureCredential $aadAdminAccount
–
And if you require to UNinstall the Azure AD Password Protection Proxy Service, then you can use the following
WMIC PRODUCT WHERE NAME="Azure AD Password Protection Proxy" CALL UNINSTALL
OR
$product = Get-WmiObject -Class win32_product -Filter "Name like ‘Azure AD Password Protection Proxy’"
$product
$product.Uninstall() # WARNING: Reboot is immediate, no mercy and no questions asked!!!
–
Have fun!
–
Cheers,
Jorge
————————————————————————————————————————————————————-
This posting is provided "AS IS" with no warranties and confers no rights!
Always evaluate/test everything yourself first before using/implementing this in production!
This is today’s opinion/technology, it might be different tomorrow and will definitely be different in 10 years!
DISCLAIMER: https://jorgequestforknowledge.wordpress.com/disclaimer/
————————————————————————————————————————————————————-
########################### Jorge’s Quest For Knowledge ##########################
#################### http://JorgeQuestForKnowledge.wordpress.com/ ###################
————————————————————————————————————————————————————-