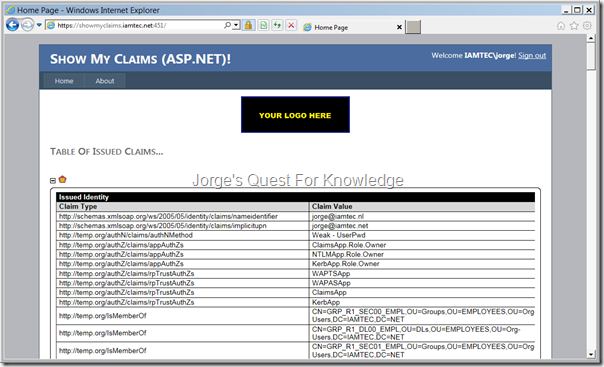
On the page “How to configure hybrid Azure Active Directory joined devices” Microsoft explains how to setup Domain Join ++, currently a.k.a. Hybrid AAD Join. This post is about, hopefully giving additional, clarification on how to setup the claims rules in ADFS. All the scenarios listed below work, it just on your scenario. Feel free to leave any comments if unclear. The import of the rules below should replace your current rules for the AAD RP Trust, and where applicable add rules to your AD CP trust. A final note, is that these rule sets are based upon Microsoft’s rule in the previous article.
Make sure to test this first in your test environment!
You may also want to have a look at the following blog post:
(2016-12-16) Automatic Azure AD Join With ADFS v3.0 And Higher And Conditional Access – What You Really Need In Detail
–
[OPTION 1]
The following works if you have claims rules in place on the AD CP trust that output the following claim types. This is true if you are using the default claim rule set in ADFSv3/ADFSv4:
–
Assumptions here:
- You have one ADFS environment servicing all the federated domains in AAD
- The federation identifier being used on your federated domains in AAD is default
- The primary group was not changed for any user or any computer
- The objectGUID is the attribute being used for the Immutable ID for users
- The objectGUID is the attribute being used for the Immutable ID for computers
- On-premises UPN is also the UPN used in AAD
- Whether or not you have multiple federated domains, the config below for the IssuerID for users works as long as the UPN of the user matches one of the federated domains in AAD
- You will replace FEDERATED-DOMAIN with one of the federated domains in AAD. It does not matter which one
- You will replace NAME-OF-AAD/O365-RP-TRUST with the actual name of the RP trust for AAD/O365
–
Remarks:
- Leave a comment if you have any deviation of the assumptions above
–
Thoughts here:
- It is making multiple LDAP calls to AD, and is therefore not that optimized. It works though!
- Still using groupsid claim type
–
Link to claims rules below: https://www.dropbox.com/s/vgzvnwhku2adp39/AzureAD-RP-Trust-Issuance-Rules1.txt
–
$aadRPTrustIssuanceRules = @"
@RuleName = "Issue UPN And ImmutableID (Domain User Only)"
c1:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-513$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"] &&
c2:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname"%5D
=> issue(store = "Active Directory", types = ("http://schemas.xmlsoap.org/claims/UPN", "http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID"), query = ";userPrincipalName,objectGUID;{0}", param = c2.Value);
@RuleName = "Issue IssuerID (Domain User Only)"
c:[Type == "http://schemas.xmlsoap.org/claims/UPN"%5D
=> issue(Type = "http://schemas.microsoft.com/ws/2008/06/identity/claims/issuerid", Value = regexreplace(c.Value, ".+@(?<domain>.+)", http://${domain}/adfs/services/trust/));
@RuleName = "Issue ImmutableID (Domain Joined Computer Only)"
c1:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"] &&
c2:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(store = "Active Directory", types = ("http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID"), query = ";objectguid;{0}", param = c2.Value);
@RuleName = "Issue Account Type (Domain Joined Computer Only)"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(Type = "http://schemas.microsoft.com/ws/2012/01/accounttype", Value = "DJ");
@RuleName = "Issue ObjectGUID (Domain Joined Computer Only)"
c1:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"] &&
c2:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(store = "Active Directory", types = ("http://schemas.microsoft.com/identity/claims/onpremobjectguid"), query = ";objectguid;{0}", param = c2.Value);
@RuleName = "Issue ObjectSID (Domain Joined Computer Only)"
c1:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"] &&
c2:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/primarysid", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(claim = c2);
@RuleName = "Issue IssuerID (Domain Joined Computer Only)"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(Type = "http://schemas.microsoft.com/ws/2008/06/identity/claims/issuerid", Value = http://FEDERATED-DOMAIN/adfs/services/trust/);
@RuleName = "Issue NameID (Domain User and Domain Joined Computer)"
c:[Type == "http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID"%5D
=> issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"%5D = "urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified");
@RuleName = "Issue AuthN Methods References (Domain User and Domain Joined Computer)"
c:[Type == "http://schemas.microsoft.com/claims/authnmethodsreferences"%5D
=> issue(claim = c);
"@
Set-AdfsRelyingPartyTrust -TargetName "NAME-OF-AAD/O365-RP-TRUST" -IssuanceTransformRules $aadRPTrustIssuanceRules
–
[OPTION 2]
The following works if you have claims rules in place on the AD CP trust that output the following claim types. This is true if you are using the default claim rule set in ADFSv3/ADFSv4:
–
Assumptions here:
- You have one ADFS environment servicing all the federated domains in AAD
- The federation identifier being used on your federated domains in AAD is default
- The primary group was not changed for any user or any computer
- The objectGUID is the attribute being used for the Immutable ID for users
- The objectGUID is the attribute being used for the Immutable ID for computers
- On-premises UPN is also the UPN used in AAD
- Whether or not you have multiple federated domains, the config below for the IssuerID for users works as long as the UPN of the user matches one of the federated domains in AAD
- You will replace FEDERATED-DOMAIN with one of the federated domains in AAD. It does not matter which one
- You will replace NAME-OF-AAD/O365-RP-TRUST with the actual name of the RP trust for AAD/O365
–
Remarks:
- Leave a comment if you have any deviation of the assumptions above
–
Thoughts here:
- Although a few LDAP calls less, it is still making LDAP calls to AD. It works though!
- Still using groupsid claim type
–
Link to claims rules below: https://www.dropbox.com/s/udn1rudm5bgv7jq/AzureAD-RP-Trust-Issuance-Rules2.txt
–
$aadRPTrustIssuanceRules = @"
@RuleName = "Issue UPN (Domain User Only)"
c1:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-513$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"] &&
c2:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"%5D
=> issue(Type = "http://schemas.xmlsoap.org/claims/UPN", Issuer = c2.Issuer, OriginalIssuer = c2.OriginalIssuer, Value = c2.Value, ValueType = c2.ValueType);
@RuleName = "Issue IssuerID (Domain User Only)"
c:[Type == "http://schemas.xmlsoap.org/claims/UPN"%5D
=> issue(Type = "http://schemas.microsoft.com/ws/2008/06/identity/claims/issuerid", Value = regexreplace(c.Value, ".+@(?<domain>.+)", http://${domain}/adfs/services/trust/));
@RuleName = "Issue Account Type (Domain Joined Computer Only)"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(Type = "http://schemas.microsoft.com/ws/2012/01/accounttype", Value = "DJ");
@RuleName = "Issue ObjectGUID (Domain Joined Computer Only)"
c1:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"] &&
c2:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(store = "Active Directory", types = ("http://schemas.microsoft.com/identity/claims/onpremobjectguid"), query = ";objectguid;{0}", param = c2.Value);
@RuleName = "Issue ObjectSID (Domain Joined Computer Only)"
c1:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"] &&
c2:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/primarysid", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(claim = c2);
@RuleName = "Issue IssuerID (Domain Joined Computer Only)"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(Type = "http://schemas.microsoft.com/ws/2008/06/identity/claims/issuerid", Value = http://FEDERATED-DOMAIN/adfs/services/trust/);
@RuleName = "ImmutableID (Domain User And Domain Joined Computer)"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname"%5D
=> issue(store = "Active Directory", types = ("http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID"), query = ";objectGUID;{0}", param = c.Value);
@RuleName = "Issue NameID (Domain User and Domain Joined Computer)"
c:[Type == "http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID"%5D
=> issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"%5D = "urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified");
@RuleName = "Issue AuthN Methods References (Domain User and Domain Joined Computer)"
c:[Type == "http://schemas.microsoft.com/claims/authnmethodsreferences"%5D
=> issue(claim = c);
"@
Set-AdfsRelyingPartyTrust -TargetName "NAME-OF-AAD/O365-RP-TRUST" -IssuanceTransformRules $aadRPTrustIssuanceRules
–
[OPTION 3]
The following works if you have claims rules in place on the AD CP trust that output the following claim types. This is true if you are using the default claim rule set in ADFSv3/ADFSv4:
–
For the last claim type you would need the following claim rule on the AD CP trust if you are not already extracting additional data from AD
–
$additionalADCPTrustRule = @"
@RuleTemplate = "LdapClaims"
@RuleName = "Extract Extra Data From AD"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> issue(store = "Active Directory", types = ("http://temp.org/identity/claims/objectGUID"), query = ";objectguid;{0}", param = c.Value);
"@
$existingADCPtrustAcceptRuleSet = (Get-AdfsClaimsProviderTrust -Name "Active Directory").AcceptanceTransformRules
$newADCPtrustAcceptRuleSet = $existingADCPtrustAcceptRuleSet + $additionalADCPTrustRule
Set-AdfsClaimsProviderTrust -TargetName "Active Directory" -AcceptanceTransformRules $newADCPtrustAcceptRuleSet
–
If you are already extracting additional data from AD, you need to add the claim type and attribute to that existing extraction
–
Assumptions here:
- You have one ADFS environment servicing all the federated domains in AAD
- The federation identifier being used on your federated domains in AAD is default
- The primary group was not changed for any user or any computer
- The objectGUID is the attribute being used for the Immutable ID for users
- The objectGUID is the attribute being used for the Immutable ID for computers
- On-premises UPN is also the UPN used in AAD
- Whether or not you have multiple federated domains, the config below for the IssuerID for users works as long as the UPN of the user matches one of the federated domains in AAD
- You will replace FEDERATED-DOMAIN with one of the federated domains in AAD. It does not matter which one
- You will replace NAME-OF-AAD/O365-RP-TRUST with the actual name of the RP trust for AAD/O365
–
Remarks:
- Leave a comment if you have any deviation of the assumptions above
–
Thoughts here:
- No LDAP calls!
- Still using groupsid claim type
–
Link to claims rules below: https://www.dropbox.com/s/8cicjpyusapsarj/AzureAD-RP-Trust-Issuance-Rules3.txt
–
$aadRPTrustIssuanceRules = @"
@RuleName = "Issue UPN (Domain User Only)"
c1:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-513$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"] &&
c2:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"%5D
=> issue(Type = "http://schemas.xmlsoap.org/claims/UPN", Issuer = c2.Issuer, OriginalIssuer = c2.OriginalIssuer, Value = c2.Value, ValueType = c2.ValueType);
@RuleName = "Issue IssuerID (Domain User Only)"
c:[Type == "http://schemas.xmlsoap.org/claims/UPN"%5D
=> issue(Type = "http://schemas.microsoft.com/ws/2008/06/identity/claims/issuerid", Value = regexreplace(c.Value, ".+@(?<domain>.+)", http://${domain}/adfs/services/trust/));
@RuleName = "Issue Account Type (Domain Joined Computer Only)"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(Type = "http://schemas.microsoft.com/ws/2012/01/accounttype", Value = "DJ");
@RuleName = "Issue ObjectGUID (Domain Joined Computer Only)"
c1:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"] &&
c2:[Type == "http://temp.org/identity/claims/objectGUID"%5D
=> issue(Type = "http://schemas.microsoft.com/identity/claims/onpremobjectguid", Issuer = c2.Issuer, OriginalIssuer = c2.OriginalIssuer, Value = c2.Value, ValueType = c2.ValueType);
@RuleName = "Issue ObjectSID (Domain Joined Computer Only)"
c1:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"] &&
c2:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/primarysid", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(claim = c2);
@RuleName = "Issue IssuerID (Domain Joined Computer Only)"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value =~ "-515$", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(Type = "http://schemas.microsoft.com/ws/2008/06/identity/claims/issuerid", Value = http://FEDERATED-DOMAIN/adfs/services/trust/);
@RuleName = "ImmutableID (Domain User And Domain Joined Computer)"
c:[Type == "http://temp.org/identity/claims/objectGUID"%5D
=> issue(Type = "http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType);
@RuleName = "Issue NameID (Domain User and Domain Joined Computer)"
c:[Type == "http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID"%5D
=> issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"%5D = "urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified");
@RuleName = "Issue AuthN Methods References (Domain User and Domain Joined Computer)"
c:[Type == "http://schemas.microsoft.com/claims/authnmethodsreferences"%5D
=> issue(claim = c);
"@
Set-AdfsRelyingPartyTrust -TargetName "NAME-OF-AAD/O365-RP-TRUST" -IssuanceTransformRules $aadRPTrustIssuanceRules
–
[OPTION 4]
The following works if you have claims rules in place on the AD CP trust that output the following claim types. This is true if you are using the default claim rule set in ADFSv3/ADFSv4 for the first 2 claim types, but not for the last 2 claim types. My main reason for not using groupsid is that the amount of values can be so huge it may not fit on a cookie and the browser chokes. Because of that, when not using the groupsid claim type, you need to design a better model to extract group data from AD and use authorization based claims types from that data. If you are not using the groupsid claim type you can also not identify the difference between a user and a computer. That’s why you can then specifically extract the primaryGroupID.:
–
For the last 2 claim types you would need the following claim rule on the AD CP trust if you are not already extracting additional data from AD
–
$additionalADCPTrustRule = @"
@RuleTemplate = "LdapClaims"
@RuleName = "Extract Extra Data From AD"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> issue(store = "Active Directory", types = ("http://temp.org/identity/claims/objectGUID","http://temp.org/identity/claims/primaryGroupID"), query = ";objectguid,primaryGroupID;{0}", param = c.Value);
"@
$existingADCPtrustAcceptRuleSet = (Get-AdfsClaimsProviderTrust -Name "Active Directory").AcceptanceTransformRules
$newADCPtrustAcceptRuleSet = $existingADCPtrustAcceptRuleSet + $additionalADCPTrustRule
Set-AdfsClaimsProviderTrust -TargetName "Active Directory" -AcceptanceTransformRules $newADCPtrustAcceptRuleSet
–
If you are already extracting additional data from AD, you need to add the claim type and attribute to that existing extraction
–
Assumptions here:
- You have one ADFS environment servicing all the federated domains in AAD
- The federation identifier being used on your federated domains in AAD is default
- The primary group was not changed for any user or any computer
- The objectGUID is the attribute being used for the Immutable ID for users
- The objectGUID is the attribute being used for the Immutable ID for computers
- On-premises UPN is also the UPN used in AAD
- Whether or not you have multiple federated domains, the config below for the IssuerID for users works as long as the UPN of the user matches one of the federated domains in AAD
- You will replace FEDERATED-DOMAIN with one of the federated domains in AAD. It does not matter which one
- You will replace NAME-OF-AAD/O365-RP-TRUST with the actual name of the RP trust for AAD/O365
–
Remarks:
- Leave a comment if you have any deviation of the assumptions above
–
Thoughts here:
- No LDAP calls!
- No groupsid claim type!
–
Link to claims rules below: https://www.dropbox.com/s/6nbwuuxl677wb3p/AzureAD-RP-Trust-Issuance-Rules4.txt
–
$aadRPTrustIssuanceRules = @"
@RuleName = "Issue UPN (Domain User Only)"
c1:[Type == "http://temp.org/identity/claims/primaryGroupID", Value =~ "^513$"] &&
c2:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"%5D
=> issue(Type = "http://schemas.xmlsoap.org/claims/UPN", Issuer = c2.Issuer, OriginalIssuer = c2.OriginalIssuer, Value = c2.Value, ValueType = c2.ValueType);
@RuleName = "Issue IssuerID (Domain User Only)"
c:[Type == "http://schemas.xmlsoap.org/claims/UPN"%5D
=> issue(Type = "http://schemas.microsoft.com/ws/2008/06/identity/claims/issuerid", Value = regexreplace(c.Value, ".+@(?<domain>.+)", http://${domain}/adfs/services/trust/));
@RuleName = "Issue Account Type (Domain Joined Computer Only)"
c:[Type == "http://temp.org/identity/claims/primaryGroupID", Value =~ "^515$"]
=> issue(Type = "http://schemas.microsoft.com/ws/2012/01/accounttype", Value = "DJ");
@RuleName = "Issue ObjectGUID (Domain Joined Computer Only)"
c1:[Type == "http://temp.org/identity/claims/primaryGroupID", Value =~ "^515$"] &&
c2:[Type == "http://temp.org/identity/claims/objectGUID"%5D
=> issue(Type = "http://schemas.microsoft.com/identity/claims/onpremobjectguid", Issuer = c2.Issuer, OriginalIssuer = c2.OriginalIssuer, Value = c2.Value, ValueType = c2.ValueType);
@RuleName = "Issue ObjectSID (Domain Joined Computer Only)"
c1:[Type == "http://temp.org/identity/claims/primaryGroupID", Value =~ "^515$"] &&
c2:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/primarysid", Issuer =~ "^(AD AUTHORITY|SELF AUTHORITY|LOCAL AUTHORITY)$"]
=> issue(claim = c2);
@RuleName = "Issue IssuerID (Domain Joined Computer Only)"
c:[Type == "http://temp.org/identity/claims/primaryGroupID", Value =~ "^515$"]
=> issue(Type = "http://schemas.microsoft.com/ws/2008/06/identity/claims/issuerid", Value = http://FEDERATED-DOMAIN/adfs/services/trust/);
@RuleName = "ImmutableID (Domain User And Domain Joined Computer)"
c:[Type == "http://temp.org/identity/claims/objectGUID"%5D
=> issue(Type = "http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType);
@RuleName = "Issue NameID (Domain User and Domain Joined Computer)"
c:[Type == "http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID"%5D
=> issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"%5D = "urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified");
@RuleName = "Issue AuthN Methods References (Domain User and Domain Joined Computer)"
c:[Type == "http://schemas.microsoft.com/claims/authnmethodsreferences"%5D
=> issue(claim = c);
"@
Set-AdfsRelyingPartyTrust -TargetName "NAME-OF-AAD/O365-RP-TRUST" -IssuanceTransformRules $aadRPTrustIssuanceRules
–
Hopefully this blog post gives you the information you need to understand what is needed
–
Cheers,
Jorge
————————————————————————————————————————————————————-
This posting is provided "AS IS" with no warranties and confers no rights!
Always evaluate/test everything yourself first before using/implementing this in production!
This is today’s opinion/technology, it might be different tomorrow and will definitely be different in 10 years!
DISCLAIMER: https://jorgequestforknowledge.wordpress.com/disclaimer/
————————————————————————————————————————————————————-
########################### Jorge’s Quest For Knowledge ##########################
#################### http://JorgeQuestForKnowledge.wordpress.com/ ###################
————————————————————————————————————————————————————-