As mentioned in the previous post, (2013-08-24) Enabling Key Counting With A CSP Not Supporting It Results In Error (0×80090029) During CA Installation/Configuration, I was rebuilding my test environment. In addition to installing and configuring a certificate authority I also wanted to install and configure an online responder. Before, I used the default “OCSP Response Signing” certificate template, but I wanted to duplicate it and create a new one. Because I install multiple environments for testing purposes I wanted to script the creation of the certificate templates so save time. I never found an easy way script the duplication of certificate templates. So I duplicated the templates first and changed the settings as needed. Then through ADSIEDIT I got the attribute values and put them in a script with ADMOD from joeware. I did this for multiple certificate templates.
The settings of the duplicated “OCSP Response Signing” certificate template are shown below.

Figure 1: The Settings Of The Duplicated “OCSP Response Signing” Certificate Template
–
ADMOD –h <FQDN DC> -mvdelim # -replacedn XXX-CONFIG-XXX:_config -add -b "CN=OCSPResponseSigning_v20,CN=Certificate Templates,CN=Public Key Services,CN=Services,XXX-CONFIG-XXX" "objectClass::pKICertificateTemplate" "displayName::OCSP Response Signing v20" "showInAdvancedViewOnly::TRUE" "flags::131648" "revision::100" "pKICriticalExtensions:++:2.5.29.15" "pKIDefaultKeySpec::2" "pKIExtendedKeyUsage:++:1.3.6.1.5.5.7.3.9" "pKIKeyUsage::8000" "pKIMaxIssuingDepth::0" "BIN##pKIExpirationPeriod::0080 37AE FFF4 FFFF" "BIN##pKIOverlapPeriod::0080 2CAB 6DFE FFFF" "pKIDefaultCSPs:++:1,Microsoft Enhanced Cryptographic Provider v1.0" "msPKI-RA-Signature::0" "msPKI-Enrollment-Flag::20512" "msPKI-Private-Key-Flag::33751040" "msPKI-Certificate-Name-Flag::402653184" "msPKI-Minimal-Key-Size::2048" "msPKI-Template-Schema-Version::3" "msPKI-Template-Minor-Revision::3" "msPKI-Cert-Template-OID::1.3.6.1.4.1.311.21.8.7425675.14461227.5065100.6342490.10430944.249.14559993.5566867" "msPKI-Certificate-Application-Policy:++:1.3.6.1.5.5.7.3.9" "msPKI-RA-Application-Policies:++:msPKI-Asymmetric-Algorithm`PZPWSTR`RSA`msPKI-Hash-Algorithm`PZPWSTR`SHA1`msPKI-Key-Security-Descriptor`PZPWSTR`D:P(A;;FA;;;BA)(A;;FA;;;SY)(A;;GR;;;S-1-5-80-3804348527-3718992918-2141599610-3686422417-2726379419)`msPKI-Key-Usage`DWORD`2`" "msPKI-Supersede-Templates:++:OCSPResponseSigning"
–
REMARK: YOU SHOULD NOT USE THIS METHOD IN YOUR TEST ENVIRONMENT TO DUPLICATE CERT TEMPLATES! I USED THIS IN MY TEST ENVIRONMENT WITH A PREDEFINED OID.
–
REMARK: I need to use the mvdelim parameter in this case and specify a new delimiter (#). The reason for that is that ADMOD by default uses the ; as a delimiter for multi-valued attributes. However, if you look at the second last attribute and its value in the command line, you will see it contains multiple ; as a value. Hence the required change in delimiter
–

Figure 2: Scripting The Creation Of The Custom “OCSP Response Signing” Certificate Template
–
Then I used DSACLS to configure the permissions of that specific certificate template.
REM Convert The DNS Domain To An NC
SET DNDOMAIN=DC=%USERDNSDOMAIN:.=,DC=%
REM Disable Inheritance And Copy The Inherited Permissions Onto The Object As Explicit Permissions
DSACLS "\\<FQDN DC>\CN=OCSPResponseSigning_v20,CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,%DNDOMAIN%" /P:Y
REM Assign Enterprise Admins Allow:Read And Allow:Write
DSACLS "\\<FQDN DC>\CN=OCSPResponseSigning_v20,CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,%DNDOMAIN%" /G "Enterprise Admins:GRWDWOWP"
REM Remove Any Assigned Permissions To Domain Admins
DSACLS "\\<FQDN DC>\CN=OCSPResponseSigning_v20,CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,%DNDOMAIN%" /R "Domain Admins"
REM Assign Domain Admins Allow:Read And Allow:Write
DSACLS "\\<FQDN DC>\CN=OCSPResponseSigning_v20,CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,%DNDOMAIN%" /G "Domain Admins:GRWDWOWP"
REM Remove Any Assigned Permissions To SYSTEM
DSACLS "\\<FQDN DC>\CN=OCSPResponseSigning_v20,CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,%DNDOMAIN%" /R "SYSTEM"
REM Assign SYSTEM Allow:Read And Allow:Write
DSACLS "\\<FQDN DC>\CN=OCSPResponseSigning_v20,CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,%DNDOMAIN%" /G "SYSTEM:GRWDWOWP"
REM Assign A Custom Group Allow:Enroll
DSACLS "\\<FQDN DC>\CN=OCSPResponseSigning_v20,CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,%DNDOMAIN%" /G "GRP_R2_PKI-CertTmplt-Subscr-OCSPResponseSigning:CA;Enroll"
The last line assigns a custom group Allow:Enroll permissions. It is NOT needed to assigned AutoEnroll permissions! The command that disables inheritance and copies the inherited permissions to become explicit permissions keeps Authenticated Users with Allow:Read. By making the computer account of my OCSP server a member of that custom group OCSP Response Signing certificates are automatically enrolled by the OCSP service.
–
The second last thing to do is to configure the CA to support the custom “OCSP Response Signing” certificate template to be able to enroll certificates derived from that certificate template. The last thing to do is to configure OCSP to support revocation information for the installed CA (see: Designing And Implementing An OCSP Responder (Series)).
So as soon as you have configured the revocation information for that specific CA (also see the series: Automated/Unattended Installation Of OCSP) and you pressed/clicked Refresh it should tell you it got a new signing certificate. However, unfortunately, the case is different. No certificate is being enrolled! Damn!
This is what you will see continuously.

Figure 3: The Online Responder Configuration – Error “Bad Signing Certificate On Array Controller”
–

Figure 4: The Online Responder Configuration – Error “Signing Certificate: Not Found”
–
When looking at the Application Event Log, you will see…

Figure 5: The Online Responder Service – Error “0x80092006: No Provider Was Specified For The Store Or Object”
–

Figure 6: The Online Responder Service – Error “0x80092006: No Provider Was Specified For The Store Or Object”
–
Both the errors do not give you a clear hint of what’s wrong.
The only thing I remembered was that when I used the default “OCSP Response Signing” certificate template everything worked like a charm! Trouble started when I used my duplicated/custom certificate template. So, the first task was to compare both settings! YOU can do the same by comparing figure 1 above and figure 7 below.

Figure 7: The Settings Of The Original “OCSP Response Signing” Certificate Template
–
Besides the “msPKI-Cert-Template-OID” attribute value being different, there is another difference! The original “OCSP Response Signing” Certificate Template DOES NOT specify a CSP, while the duplicate “OCSP Response Signing” Certificate Template does. So, where did that go wrong!?
In the GUI this looks like….


Figure 8: The Cryptography Settings Of The Default (Left) And The Duplicated (Right) “OCSP Response Signing” Certificate Template
–
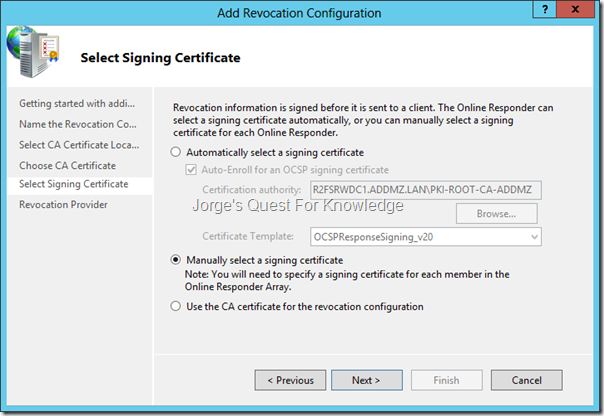
The only thing to do here is changing the cryptographic settings of the duplicated “OCSP Response Signing” Certificate Template to match those of the original “OCSP Response Signing” Certificate Template.

Figure 9: The Online Responder Configuration – “Working”
–

Figure 10: The Online Responder Configuration – “Signing Certificate: OK”
–

Figure 11: The Online Responder Configuration – Certificate Enrolled
–

Figure 12: The Online Responder Configuration – Certificate (Re)Loaded
–
Explanation of what went wrong….
As I said I was scripting the creation of certificate templates. While I was copying information around I copied the text "pKIDefaultCSPs:++:1,Microsoft Enhanced Cryptographic Provider v1.0" into the command line that creates the duplicated “OCSP Response Signing” Certificate Template. However, I SHOULD NOT have done that! It was therefore a mistake that generated the previous errors shown and that looks lots of time to troubleshoot!
So in the previous ADMOD command the part "pKIDefaultCSPs:++:1,Microsoft Enhanced Cryptographic Provider v1.0" MUST be removed!
–
Just a stupid copy/paste mistake.
–
Cheers,
Jorge
———————————————————————————————
* This posting is provided "AS IS" with no warranties and confers no rights!
* Always evaluate/test yourself before using/implementing this!
* DISCLAIMER: https://jorgequestforknowledge.wordpress.com/disclaimer/
———————————————————————————————
############### Jorge’s Quest For Knowledge #############
######### http://JorgeQuestForKnowledge.wordpress.com/ ########
———————————————————————————————





























![image_thumb141_thumb[1]_thumb_thumb_thumb image_thumb141_thumb[1]_thumb_thumb_thumb](https://jorgequestforknowledge.files.wordpress.com/2013/08/image_thumb141_thumb1_thumb_thumb_thumb_thumb.png)
![image_thumb144_thumb[1]_thumb_thumb_thumb image_thumb144_thumb[1]_thumb_thumb_thumb](https://jorgequestforknowledge.files.wordpress.com/2013/08/image_thumb144_thumb1_thumb_thumb_thumb_thumb.png)
![image_thumb147_thumb[1]_thumb_thumb_thumb image_thumb147_thumb[1]_thumb_thumb_thumb](https://jorgequestforknowledge.files.wordpress.com/2013/08/image_thumb147_thumb1_thumb_thumb_thumb_thumb.png)
![image_thumb133_thumb[1]_thumb_thumb image_thumb133_thumb[1]_thumb_thumb](https://jorgequestforknowledge.files.wordpress.com/2013/08/image_thumb133_thumb1_thumb_thumb_thumb.png)
![image_thumb137_thumb[1]_thumb_thumb image_thumb137_thumb[1]_thumb_thumb](https://jorgequestforknowledge.files.wordpress.com/2013/08/image_thumb137_thumb1_thumb_thumb_thumb.png)

![image_thumb123_thumb[1]_thumb image_thumb123_thumb[1]_thumb](https://jorgequestforknowledge.files.wordpress.com/2013/08/image_thumb123_thumb1_thumb_thumb.png)
![image_thumb127_thumb[1]_thumb image_thumb127_thumb[1]_thumb](https://jorgequestforknowledge.files.wordpress.com/2013/08/image_thumb127_thumb1_thumb_thumb.png)
![image_thumb130_thumb[1]_thumb image_thumb130_thumb[1]_thumb](https://jorgequestforknowledge.files.wordpress.com/2013/08/image_thumb130_thumb1_thumb_thumb.png)
![image_thumb112_thumb[1] image_thumb112_thumb[1]](https://jorgequestforknowledge.files.wordpress.com/2013/08/image_thumb112_thumb1_thumb.png)
![image_thumb116_thumb[1] image_thumb116_thumb[1]](https://jorgequestforknowledge.files.wordpress.com/2013/08/image_thumb116_thumb1_thumb.png)
![image_thumb120_thumb[1] image_thumb120_thumb[1]](https://jorgequestforknowledge.files.wordpress.com/2013/08/image_thumb120_thumb1_thumb.png)